The mindset shift from security to trust & safety
Why focusing on trust & safety can lead to organic risk management

Today, organizations are continuously looking for more agility and velocity. They all want to streamline their processes and become more effective at what makes them successful. This requires every department to be productive and move at the pace they can sustain while also removing any non-critical dependencies to allow for productivity to accelerate independently towards a common goal. This is often manifested by people wanting to effectively do their jobs and relying on technology to enable them to do so. This is why organizations have to focus on buying the right set of technologies that facilitate the velocity and flexibility their employees need in order to achieve their maximum output.
However, there are still security personas and programs out there that are only focused on making sure the organizations do not suffer from a severe breach. While this may sound to you like the obvious mission of a security program, it is in fact incorrect. The narrow attention to a breached vs. not breached state can create some disconnects between the outcomes mentioned above and an acceptable risk posture. In addition, a lot organizations do not understand the value of making the right technology decisions that enable their employees by the ease of use and organic fit of the technologies they procure. In fact, I have seen a huge overlap between poor IT technology decisions and a low performing security program.
While most security professionals will agree that the security function is one of risk management, in practice, they still only focus on the breached state of their organizations. When in reality, you can accomplish the goal of getting to an environment where risks are managed appropriately without making the whole organization your enemy. This requires a different mindset, though, and that is one of building systems that focus on trust and safety.
The needs of an organization
Organizations just like people have a set of needs that must be met in order to be successful. Security teams need to think of what are the current needs and meet those before building or solving for new ones. Ignoring the needs of the people will also mean a high chance of failure when trying to build any system. Some may say that there is an application of Maslow’s hierarchy of needs to organizations and therefore their security programs.
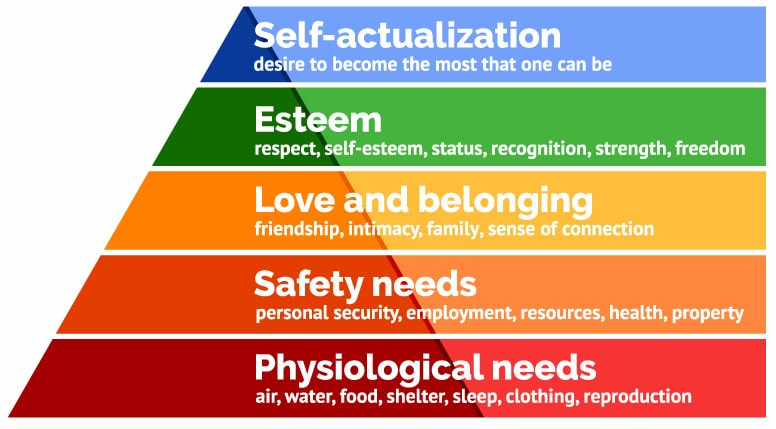
Maslow’s hierarchy of needs
Maslow’s concept is a motivational theory composed of a five-tiered model of human needs, often the hierarchical levels are presented with a pyramid. The concept that Maslow introduced is that the needs lower down in the hierarchy must be met before attending to the needs in the higher levels. While somewhat satisfying the needs of the first four levels will make them go away, the top need is a permanent one as it satisfies the needs of growth.
Hierarchy of needs in an organization
There’s quite a bit of work and research done in this area but naturally the needs of a person also apply to the workplace. Organizations need to ensure that they are meeting the physiological needs of their employees. When people feel safe (more on this later) they feel more motivated to get work done. Everyone desires to be a part of something greater, so aligning the work of every employee to the bigger picture of the organization is key. Good organizations recognize and provide rewards for those high-performers. Finally, when an employee reaches the self-actualization, they feel trusted and fully empowered to make decisions.
If you want more details, here is a good write-up on applying Maslow’s concepts to the workplace. As noted, safety is an integral need that must be met in order for employees to get to the point where they can feel that they are a part of something bigger. As a continuation to this post, I will explore how Maslow’s hierarchy of needs can also be applied to a security program.
Focusing on trust & safety
As I think of the best ways that a security team/program can gain the trust of an organization and its people, I naturally think of safety systems. People & systems within an organization want to perform what they’re meant to do with minimal interruptions and friction. And you know what? They deserve it. At a high level, if you believe that a security program’s ultimate goal is to allow your organization to operate at the highest level of acceptable risk (thanks Ian), then prioritizing safety & trust systems is critical.
By safety & trust systems I mean such systems or technology that allows people to perform their main obligations but in a manner where safety is included by default. As an example, instead of trying to train your employees to spot the one out of thousands email which includes a link that if they click on it will take your company down, how about you instead build an easy way of reporting any suspicious email (and by any I mean any) and allow the natural instinct of suspicion to kick in. Continuously telling your people that one mistake can cause critical harm will only alienate your team and build distrust because you can’t take this stance without looking at the people of your organization as potential enemies.
Another great example of a safety system that yields trust within your organization, are authentication systems. We keep telling our people that passwords are critical and that they need to be secure and that multi-factor authentication is mandatory but yet we make the experience for our employees to achieve what they will naturally want to do, which is the right thing, extremely difficult. This leads to people looking for shortcuts, naturally, and security teams complaining that people ‘do not care’. How about instead, you make very easy for your employees to authenticate in a way that is secure? Instead of spending budget on phishing simulation and triaging services, how about spending that money on physical authentication keys so that their credentials aren’t susceptible to phishing to begin with?
On a more technical side, we want our engineers to write secure code and deploy cloud infrastructure securely. But yet, the approach we take on doing that is by running scans that identify all the bad things and create a plethora of tickets for remediation. While, we may not be able to escape tickets completely, how about focusing on building or procuring products that enable developer activity with safety mechanisms turned on by default. There is no reason why a developer has to go to the AWS console to create an S3 bucket and choose secure options that may not be turned on by default when instead they can go to an internal portal and click here and there and get the same result but with security handled for them. For developers, who need to move at a certain velocity to build the products the business depends on, instead of insisting on using scanners that are ad-hoc and may not fully integrate with the systems developers use every day, how about moving more towards a model where the tools they use are utilized more (think linters, scanning from the system where the code lives) and focus more on guidance and enablement rather than gates.
And now for my final thoughts
When people are treated with respect and they have their need for safety satisfied, they will inherently trust where the safety comes from. When it comes to security and risk management, this will help open the channels of communication towards the security teams. When these channels are opened, that leads to organic risk management. In this mode of risk management, the people who are the closest to the systems or processes (basically who will know and understand the risks best) build a natural gravity towards the risk management teams. That allows proper risk identification and two-way conversation about how and whether or not the risks need to be managed instead of the security teams trying to identify every risk and miscalculate the impact and remediation of them. Every security program must aspire to achieve this level of risk management.


Definitely a rant, very myopic approach assuming everyone has the luxury of building extra layers of infra. Physical keys are not the solution either. Employees hit yubikey whenever prompted. Focus on secure by default by using whatever is available.